2.6. DomiSMP resource locator and permissions
2.6.1. Introduction
The purpose of the eDelivery Building Block is to enable the electronic exchange of digital data and documents in an interoperable, secure, reliable and trusted way for businesses and public administrations. eDelivery provides sample component implementations such as Domibus, DomiSML and DomiSMP to promote and facilitate the electronic message exchange for various participant messaging networks (also called business domains).
This document explains explans two key concepts of the DomiSMP application: The resources locator and the DomiSMP realms.
2.6.2. Purpose of this guide
This guide will help you understand DomiSMP realms such as domain, groups and resources and the access permissions. In the second part of the guide, you will learn how to locate specific resources in DomiSMP with the HTTP-GET query path.
We recommend reading from start to end for a comprehensive understanding, though you may skip to relevant sections if familiar with some concepts.
2.6.3. DomiSMP application
DomiSMP supports various network requirements, allowing for custom extensions and supporting multiple domains where each domain can have its own metadata resource types and users/network administrators.
The application is document-agnostic, allowing to publish document metadata business logic in extensions, which network users can develop independently from the core application.
Users and resources can be organised into groups, each having an SMP administrator. Groups come in handy in case of large networks spanning multiple countries, where each country can have its own SMP administrator and its own set of resources and users.
DomiSMP is shipped with a default extension for OASIS SMP 1.0/2.0 and as an experimantal feature also the OASIS CPPA3 CPP documents.
In the following sections we will explain how specific resources are located in DomiSMP and then how access to these resources is controlled.
2.6.3.1. DomiSMP realms and permissions
Within DomiSMP, resources, users, and permissions are organised into a structured framework known as realms. This section delves into the three-layer hierarchical realms of the domain, group, and resource.
2.6.3.1.1. Realms
Domain realm: The highest level, indicating the network’s business aim, like invoice exchange or health records exchange. Domain admins manage the overall structure, including authentication and authorisation methods (like PKI certificates), Participant Identifier types, and messages formats. In DomiSMP, domain admins are responsible for creating/deleting groups and assigning group admins.
Group realm: This mid-level layer consists of clusters of resources and users. It allows for the organisation of resources and users into manageable segments, particularly useful in large networks. Managed by group administrators, who can create and delete resources, but only the resource admins can edit resource documents. A group admin invites participants to the exchange network and assigns them resources where they can publish their connectivity data.
Resource realm: The most basic layer. It consists of resources and its subresources, both of which are documents describing participant connectivity capabilities. Resources are identified by unique IDs (usually matching the owner identifier) and can include formats like OASIS SMP 1.0, OASIS SMP 2.0 and CPPA3 CPP document. The resource type support is done by the DomiSMP extensions, which will be explained in one of the following user guides.
2.6.3.1.2. Permissions
Each realm has its own set of permissions, determined by the user’s role within that realm. Here’s how permissions work across different realms:
Resource realm permissions: Control over specific documents. While resource admins can modify documents, group admins can invite participants but cannot alter documents directly.
Group realm permissions: Group admins manage resources within their group, including adding or removing resources and inviting new participants.
Domain realm permissions: Domain admins have the authority to create or delete groups within their domain, assign group admins, and set the framework for the network’s operational guidelines.
In essence, the DomiSMP’s structured approach to realms and permissions facilitates a clear and manageable way to organise, access, and administer resources within the network, ensuring secure and efficient data exchange.
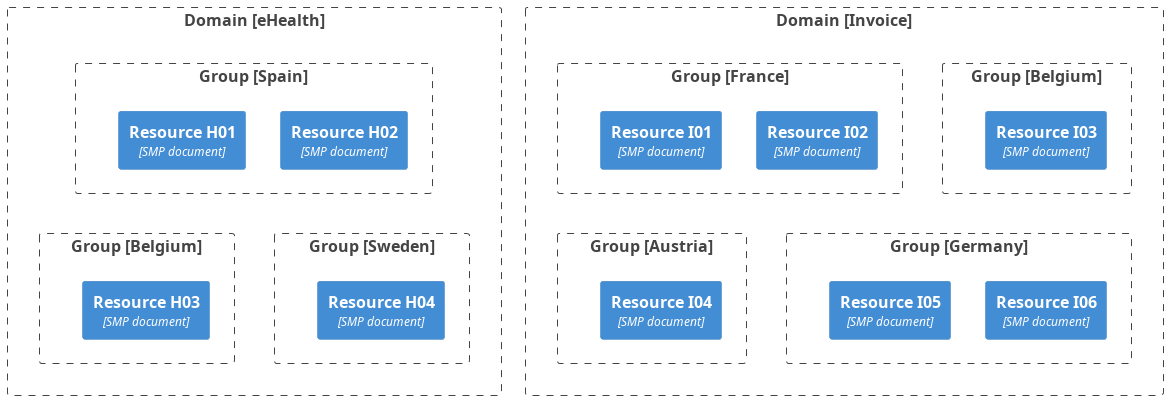
In the diagram below, see the DomiSMP realms and the relations between them. DomiSMP is the host to the domains eHealth and Invoice. The groups in each domain are organised by EU Member States: Spain, Belgium, and Sweden organise the eHealth domain, while Belgium, France, Germany, and Austria organise the Invoice domain.
2.6.3.2. DomiSMP users
In DomiSMP, users are individuals or entities with the capability to interact with and manage resources and subresources. Users can be either added manually by a system administrator or automatically through CAS, such EU Login. The permissions assigned to users depend on two factors: their role within DomiSMP and their membership within specific realms (domains, groups, and resources).
2.6.3.2.1. User application roles
The DomiSMP has two application roles which will be described below. The application roles are used to define the user’s access and control levels in the DomiSMP application.
User: The default role assigned to all new users. Initially, it offers the same permissions as an unauthenticated user. Additional privileges can be granted by assigning further roles relevant to specific realms.
System admin: This role has comprehensive control over the DomiSMP system. A system admin can configure the system settings, register new document types and extensions, and set up authentication methods for different domains.
2.6.3.2.2. DomiSMP memberships
Memberships define a user’s access level within the various realms of DomiSMP. There are two types of memberships:
Direct membership: Users directly invited to a realm have direct access to it.
Indirect membership: Users gain access through membership in a sub-realm, extending their permissions to the parent realm.
Administrators manage memberships within their respective realms. They can invite new users and assign roles, determining what the user is allowed to do within that realm. The roles and their permissions are specific to the activities within the realms of domains, groups, and resources.
2.6.4. DomiSMP membership roles
DomiSMP organises users and their access through a structured hierarchy of realms, each with distinct roles and responsibilities. This section outlines the various roles within these realms and what they allow a user to do.
2.6.4.1. Roles list
-
Anonymous: This is the default role for all unauthenticated users, providing the most basic access level.
-
Resource Viewer: Users with this role can view resources within the realms they belong to but cannot make any changes.
-
Resource Admin: Users in this role manage resources directly, capable also of editing the resource membership. Before, this role was called ServiceGroup Owner.
-
Group Viewer: Group viewers have visibility over all resources within a group but cannot modify these resources nor add/delete any.
-
Group Admin: These users manage group resources, including adding or removing resources and editing group and resource memberships. Before, this role was called SMP Admin.
-
Domain Viewer: With this role, a user can see all resources within a domain but not modify them.
-
Domain Admin: Domain admins have the highest level of control, able to create or delete domain groups, and modify domain and group memberships.
2.6.4.2. Roles overview
A user can have only one role assigned.
| Member | Resource | Group | Domain | System | |||
|---|---|---|---|---|---|---|---|
Action |
Viewer |
Admin |
Viewer |
Admin |
Viewer |
Admin |
Admin |
Domain: |
✓ |
||||||
Domain: |
✓ |
||||||
Domain: |
✓ |
✓ |
|||||
Domain Group: |
✓ |
||||||
Domain Group: |
✓ |
||||||
Domain : |
✓ |
✓ |
|||||
Resource: |
✓ |
||||||
Resource: |
✓ |
||||||
Resource: |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
✓ |
Members: |
x |
✓ (to resource) |
✓ (to resource) |
✓ |
✓ |
x |
x |
Members: |
x |
x |
x |
✓ |
✓ |
x |
x |
2.6.4.3. Membership organisation
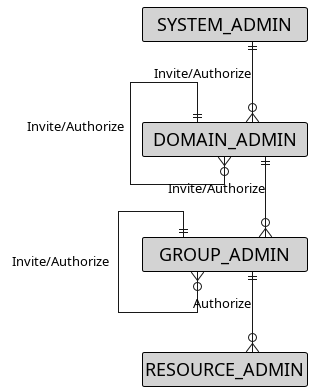
The membership model in DomiSMP is hierarchical. At the top, System Admins have the authority to add new members across DomiSMP domains. Each domain, managed by Domain Admins, can contain multiple groups. Domain Admins are responsible for creating groups and appointing Group Admins. Group Admins, in turn, can invite members to their groups and assign specific resources. This structure ensures a clear and organised way to manage DomiSMP users and their permissions.
Below, we detail this structure in a diagram, which presents the hierarchical roles that define the user’s access and control levels in DomiSMP.
2.6.4.4. DomiSMP resource and subresources
In DomiSMP, resources refer to documents that contain information about the services a participant offers. These are often in XML format but can also be in JSON, YAML, or other document types. The DomiSMP administrator assigns a resource to an end-user (the resource owner), who then updates and publishes their connectivity capabilities within this resource. Resources may contain subresources or documents to further organise connectivity capabilities.
2.6.4.5. DomiSMP resource locator coordinates
In DomiSMP, finding and identifying specific resources or subresources is done through a set of unique identifiers known as resource locator coordinates. This method is inspired by Maven’s locator, where identifiers like groupId, artifactId, version, and packaging help locate a specific resource, such as library, plugin or project. Similarly, DomiSMP uses these coordinates to pinpoint resources within its system.
The DomiSMP resource locator coordinates include the following:
-
DomainCode (Optional): Identifier for the domain within DomiSMP. If not specified, DomiSMP uses the default domain.
-
ResourceType (Optional): Identifies the kind of resource. If not defined, the default resource type is applied.
-
ResourceIdentifier (Mandatory): Identifier of the resource. In most networks, it matches the Participant Identifier; for example
urn:oasis:names:tc:ebcore:partyid-type:iso6523:0088:test1234. -
SubResourceType (Mandatory if SubResourceIdentifier is defined): Subtype of the resource for more granular identification.
-
SubResourceIdentifier (Optional): Identifier of the subresource. Further specifies the subresource, used in conjunction with SubResourceType.
To access a document within DomiSMP, an HTTP GET request is formed using a URL pattern that incorporates these coordinates. The structure for this request is:
<DomiSMP-URL>/[{DomainCode}/][{ResourceType}/]{ResourceIdentifier}[/{SubResourceType}/{SubResourceIdentifier}]
For scenarios where HTTP headers are preferable for specifying the domain and resource type, DomiSMP accommodates this through the Domain and Resource-Type headers. When used, these headers take precedence over URL path parameters, which in this case must not be used!
2.6.4.5.1. Example 1: Retrieving the resource
In this example, we demonstrate how to access a specific document from DomiSMP using the wget command. The document in question is an OASIS SMP 1.0 ServiceGroup document for a counterparty identified by urn:oasis:names:tc:ebcore:partyid-type:iso6523:0088:test1234 within the Invoice domain.
To access this document from DomiSMP, whose instance is located at the URL http://localhost:8080/, and assuming invoice-domain is the domain code for the Invoice domain and smp-1 is the code for the OASIS SMP 1.0 ServiceGroup document type, use the following wget command:
wget http://localhost:8080/invoice-domain/smp-1/urn:oasis:names:tc:ebcore:partyid-type:iso6523:0088:test1234
However, if invoice-domain is the default domain for the DomiSMP instance and OASIS SMP 1.0 is the default document type within this domain, you can simplify the command by omitting the domain and document type codes:
wget http://localhost:8080/urn:oasis:names:tc:ebcore:partyid-type:iso6523:0088:test1234
This simplified command fetches the desired document based on the assumption that the default settings in DomiSMP match the required domain and document type for this retrieval.
2.6.4.5.2. Example 2: Retrieving the subresource
Let’s say Party A wants to obtain a specific OASIS SMP 1.0 ServiceMetadata document for Party B. The document’s identifier is busdox-docid-qns::invoice-v01, and Party B’s identifier is urn:oasis:names:tc:ebcore:partyid-type:iso6523:0088:test1234. This operation occurs within the Invoice domain of the DomiSMP, accessible at the URL http://localhost:8080/. For this domain, the SMP instance code is invoice-domain, and the document type code for OASIS SMP 1.0 ServiceGroup documents is smp-1. The subresource code is services.
To retrieve the document, use the following command:
wget http://localhost:8080/invoice-domain/smp-1/urn:oasis:names:tc:ebcore:partyid-type:iso6523:0088:test1234/services/busdox-docid-qns::invoice-v01
However, if invoice-domain and OASIS SMP 1.0 are the default domain and document type within your DomiSMP instance, you can shorten your request. The shorter version does not require specifying the domain and document type codes:
wget http://localhost:8080/urn:oasis:names:tc:ebcore:partyid-type:iso6523:0088:test1234/services/busdox-docid-qns::invoice-v01
This simplified command retrieves the same OASIS SMP 1.0 ServiceMetadata document for the specified resource identifier.
2.6.4.5.3. Resolving location vector coordinates in DomiSMP
To accurately find a resource or subresource, DomiSMP uses location vector coordinates. Here’s how the process works:
DomiSMP begins by breaking down the URL into its path components. If the URL has more than five parameters, DomiSMP returns an error. Parameters are resolved one by one, to determine domain, resource type, etc. If any parameter cannot be resolved, the process halts and an error is thrown.
The process in presented in the diagram below:
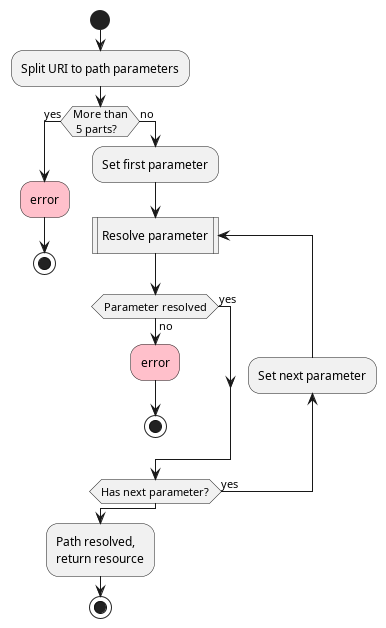
Initially, DomiSMP attempts to determine the domain. If Domain is specified through an HTTP header, that value is used directly. If no domain code matches or is provided, DomiSMP checks the first URL parameter against registered domains. Failing a match, it defaults to a pre-configured domain in the DomiSMP settings. This process ensures that the resource lookup aligns with the correct domain context, whether specified explicitly or inferred by the system defaults.
Identifying the resource type occurs after determining the domain. If the domain is specified in a path parameter, DomiSMP attempts to identify the resource type based on the next path parameter.
This is the order in which DomiSMP resolves the resource type:
-
Default setting: If the domain has only one registered resource type, this type is automatically assigned (legacy).
-
HTTP header: DomiSMP looks for a
Resource-TypeHTTP header. If the header specifies an invalid type, an error is generated. -
URL path parameter: In this case, the path must contain at least two parameters.
-
Default resource type for domain: If no specific type is found, DomiSMP uses the default type configured for the domain.
-
First registered type: In the absence of a specified default, the first type registered for the domain is used.
Note: To accommodate simultaneous use of URL path parameters and HTTP headers, if the current path parameter matches the resource type and more than two path parameters remain, DomiSMP skips the current parameter and proceeds to resolve the next.
The DomiSMP carefully analyses the current path parameter to accurately identify the resource linked with the domain and document type. Should the resource identifier not be located, DomiSMP will return an error. Conversely, if the identifier is successfully found and it represents the last parameter in the path, DomiSMP will directly return the resource document. However, if there are additional parameters, DomiSMP proceeds to determine the subresource by evaluating the last two parameters.
When locating a subresource, DomiSMP examines the final two path parameters provided in the request URL. These parameters correspond to the type and identifier of the subresource.
If both the subresource type and the subresource identifier cannot be located, DomiSMP returns an error. Otherwise, if they are found, the process yields the corresponding subresource document.
2.6.4.5.4. Path options
DomiSMP provides flexible ways to locate resources and subresources through different HTTP path configurations. Depending on the information available and specific needs, you can use one of the following path options to access the desired document.
The path options accommodate various combinations of domain codes, resource types, resource identifiers and subresource identifiers.
Please note that for options 2, 3 and 4, two variants of the path parameters are possible: if the first path variant does not give results, DomiSMP tries with the second path variant.
Here’s a guide to using these path options.
Variants -SubResourceType mandatory
-
1 path parameter: Use only the resource identifier in the URL path. If the domain or resource type isn’t specified, DomiSMP will use default settings or those provided via HTTP headers.
{ResourceIdentifier} -
2 path parameters: Include either the domain code or resource type along with the resource identifier. Missing values default to HTTP headers or DomiSMP defaults.
/{DomainCode}/{ResourceIdentifier} /{ResourceType}/{ResourceIdentifier} -
3 path parameters: Specify the domain code, resource type, and resource identifier. This configuration can also represent a resource identifier followed by subresource type and identifier if the domain and resource type are set by default or HTTP headers.
/{DomainCode}/{ResourceType}/{ResourceIdentifier} /{ResourceIdentifier}/{SubResourceType}/{SubResourceIdentifier} -
4 path parameters: This option covers cases where one value (domain or resource type) is set by default or HTTP headers, and you’re including resource and subresource identifiers.
/{DomainCode}/{ResourceIdentifier}/{SubResourceType}/{SubResourceIdentifier} /{ResourceType}/{ResourceIdentifier}/{SubResourceType}/{SubResourceIdentifier} -
5 path parameters: Use this when specifying all identifiers explicitly, including domain code, resource type, resource and subresource identifiers.
/{DomainCode}/{ResourceType}/{ResourceIdentifier}/{SubResourceType}/{SubResourceIdentifier}
2.6.4.5.5. Path examples
This section illustrates how to construct URLs for accessing resources in DomiSMP, using OASIS SMP 1.0 and OASIS SMP 2.0 documents as examples.
Note that your DomiSMP setup should have a default domain and resource type that match your intended document type (either OASIS SMP 1.0 or OASIS SMP 2.0) for these examples to apply directly.
The path is built in the following way:
{ResourceIdentifier}[/services/{SubResourceIdentifier}]
You can retrieve ServiceGroup documents by specifying the resource identifier directly in the URL. If the domain and resource type match the default settings, you don’t need to specify them in your request.
Example for a ServiceGroup document:
/iso6523-actorid-upis::0088:test1234
And if you’re specifying a domain and resource type explicitly:
/invoice-domain/smp-1/iso6523-actorid-upis::0088:test1234
To access a ServiceMetadata document, include the subresource type and identifier in the URL. busdox-docid-qns::invoice-v01 is our resource identifier. Like with ServiceGroup documents, you can omit domain and resource type if they are the default.
Example for a ServiceMetadata document:
/iso6523-actorid-upis::0088:test1234/services/busdox-docid-qns::invoice-v01
With explicit domain and resource type:
/invoice-domain/smp-1/iso6523-actorid-upis::0088:test1234/services/busdox-docid-qns::invoice-v01
The path is similar:
oasis-bdxr-smp-2/{ResourceIdentifier}/{services}/{SubResourceIdentifier}
Example for accessing an OASIS SMP 2.0 ServiceGroup document with the resource identifier iso6523-actorid-upis::0088:test1234:
/oasis-bdxr-smp-2/iso6523-actorid-upis::0088:test1234
And with a specified domain and resource type:
/invoice-domain/oasis-bdxr-smp-2/iso6523-actorid-upis::0088:test1234
Example for accessing an OASIS SMP 2.0 ServiceMetadata document with busdox-docid-qns::invoice-v01 as the subresource identifier:
/oasis-bdxr-smp-2/iso6523-actorid-upis::0088:test1234/services/busdox-docid-qns::invoice-v01
The previous example included already the resource type. Here is an example with a defined domain:
/invoice-domain/oasis-bdxr-smp-2/iso6523-actorid-upis::0088:test1234/services/busdox-docid-qns::invoice-v01
Let’s break this path down:
-
invoice-domainis the domain. -
oasis-bdxr-smp-2is the resource type. -
iso6523-actorid-upis::0088:test1234is the resource identifier. -
servicesis the subresource type. -
busdox-docid-qns::invoice-v01is the subresource identifier.